General Overview & Concept
Initial situation – Internet of Things and Artificial Intelligence
In recent years, technological development in consumer electronics and industrial applications has developed rapidly. More and smaller, networked devices are able to collect and process data anywhere. The Internet of Things (IoT) is a revolutionary change for many sectors like healthcare, building, automotive, railway, etc. Some developments are technologically amazing and frightening at the same time. Examples are fitness trackers, small devices that measure your movements and motions with help of integrated sensors. They can improve health by measuring your physical activities, measure your sleep quality etc. However, in 2018, the use of such fitness trackers has revealed secret locations of US military bases worldwide by publishing the regular jogging routes of soldiers on the Internet. [1] Information that would never have been stored a decade ago is now publicly available. The availability of those amounts of data also goes hand in hand with the development of Artificial Intelligence (AI) and Machine Learning (ML) algorithms to process them. With their use, faces of your friends can be recognized automatically in your online photo album or devices in the household can be simply controlled via voice recognition. The other side of the coin is the vulnerability of these devices in terms of security. Recent hacks of millions of webcams, printers, children’s toys and even vacuum cleaners as well as Distributed Denial-of-service (DDoS) attacks reduce confidence in this technology. In addition, users are challenged to understand and trust their increasingly complex and smart devices, sometimes resulting in mistrust, usage hesitation and even rejection.
Going to the edge – Bringing Internet of Things and Artificial Intelligence together
The developments described above mostly cover processing of data in centralized cloud locations and hence cannot be used for applications where milliseconds matter or for safety-critical applications. By moving AI to the edge, i.e. processing data locally on a hardware device, real-time applications for self-driving cars, robots and many other areas in industry can be enabled. The push of AI towards the edge can also be seen by recent announcements in consumer electronics. Google has reduced the size of the cloud-based AI voice recognition model from 2 GB to only 80 MB, so that it can also be used on embedded devices and does not need Internet connection [2]. The technological race to bringing AI to the edge can also be seen by very recent developments of hardware manufacturers. In October 2018, Google released Edge TPU [3], a custom processor to run the specific TensorFlow Lite models on edge devices. Many other, mostly US companies like Gyrfalcon, Mythic and Syntiant are also developing custom silicon for the edge.
AI + IoT = AIoT
The InSecTT partners believe that Artificial Intelligence of Things (AIoT) is the natural evolution for both AI and IoT because they are mutually beneficial. AI increases the value of the IoT through machine learning by transforming the data into useful information knowledge, while the IoT increases the value of AI through connectivity and data exchange.
Overall Objectives of InSecTT – Competitiveness for strong European Industry
The overall objectives of InSecTT are to develop solutions for (1) Intelligent, (2) Secure, (3) Trustable (4) Things applied in (5) industrial solutions for European industry throughout the whole Supply Chain (6). More precisely:
- Providing intelligent processing of data applications and communication characteristics locally at the edge to enable real-time and safety-critical industrial applications
- Developing industrial-grade secure, safe and reliable solutions that can cope with cyberattacks and difficult network conditions
- Providing measures to increase trust for user acceptance, make AI/ML explainable and give the user control over AI functionality
- Developing solutions for Internet of Things, i.e. mostly wireless devices with energy- and processing-constraints, in heterogeneous and also hostile/harsh environments
- Providing re-usable solutions across industrial domains
- Methodological approach with the Integral Supply Chain, from academic, to system designers and integrators, to component providers, applications and services developers & providers and end users
- The issues of ethics and public trust in deployed AI systems are now receiving significant international interest. The European Commission has recently released ethics guidelines for trustworthy AI. Trustworthy AI has three components: it should be lawful, it should be ethical, and it should be robust. In InSecTT, we focus on robustness and ethics, ensuring our developed systems are resilient, secure and reliable, while prioritising the principles of explainability
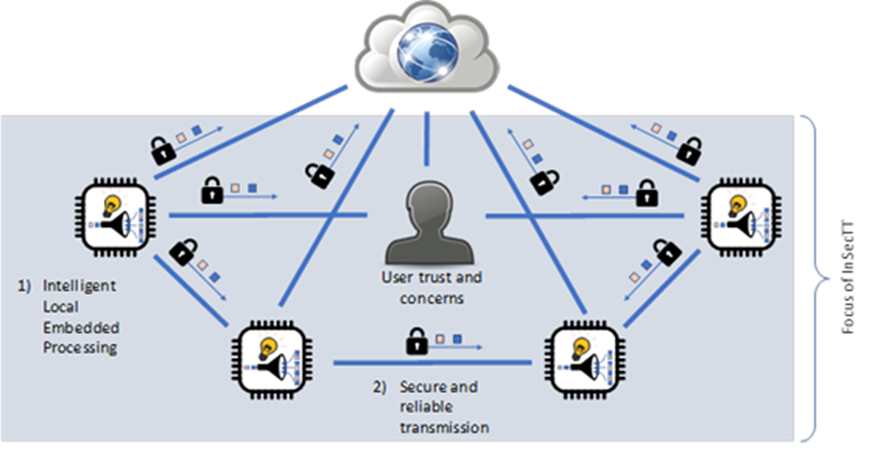
The first picture gives an overview of the focus of InSecTT. Local intelligent processing makes it possible to reduce the data required for transmission. Although most of work will be done on local level, communication with a cloud is not excluded and will be needed in the right balance in some use cases. User trust and concern considerations will be incorporated throughout the design, development, and evaluation processes to ensure trustworthiness and acceptance
Today, the development of IoT devices is already so complex that human errors inevitably occur in the conventional development process during their development. This is often exploited by resourceful hackers to compromise security and consequently leads to a loss of consumer trust. By using AI, a completely new approach is taken. The burden of finding solutions to complex problems will be transferred from the programmer to their program.
InSecTT is therefore utilizing AI for two core tasks:
- AI-supported Embedded Processing for industrial tasks: This does not only include the typical speech and image recognition tasks that AI is used for today, but also specific smaller control and monitoring tasks needed in industry and multiple instances of the most traditional ones (audio and video) cross-correlated with other monitoring techniques.
- AI enhanced wireless transmission (beam-forming, propagation, prediction, interference reduction, energy saving, opportunistic transmission, improved direction of arrival estimations, improved human safety operation,…) for improving reliability as well as security (e.g. intrusion detection and response) in heterogeneous and even hostile environments (e.g. crowded urban areas, under water and metallic environment).